One of our goals is sharing with the security community as much as we learn from VirusTotal’s data to help stop, monitor and mitigate malicious activity. When looking back to 2022 we observe different interesting trends; we decided to go deeper into the three most interesting ones: evolution of distribution vectors, trending malware artifacts and toolsets, and threat landscape evolution.
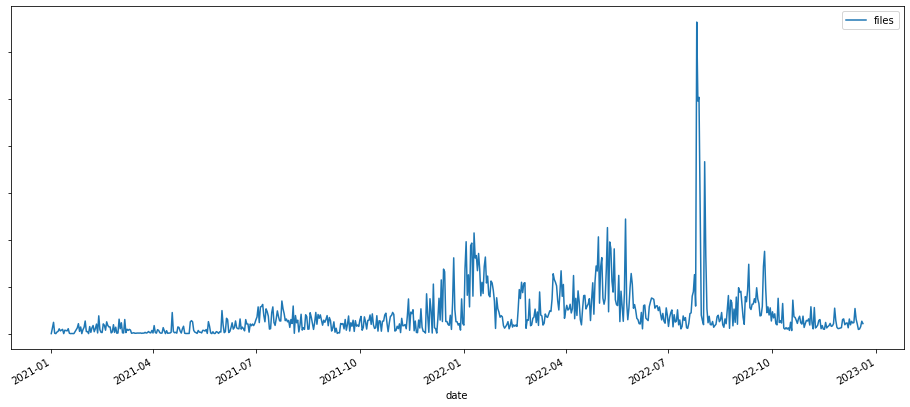
This seems to correlate with the huge increase (almost doubled compared to 2021) of malicious PDF files hosted in phishing URLs. Probably this combination was one of the main distribution vectors of fraudulent content in 2022.
Malicious PDFs hosted in phishing sites
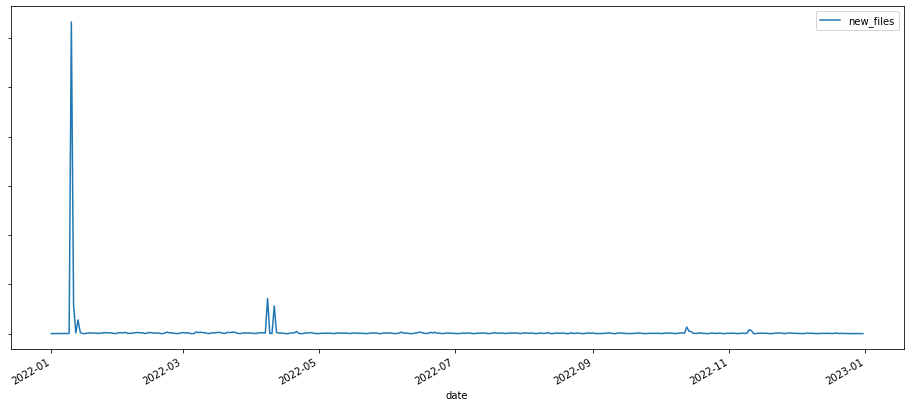
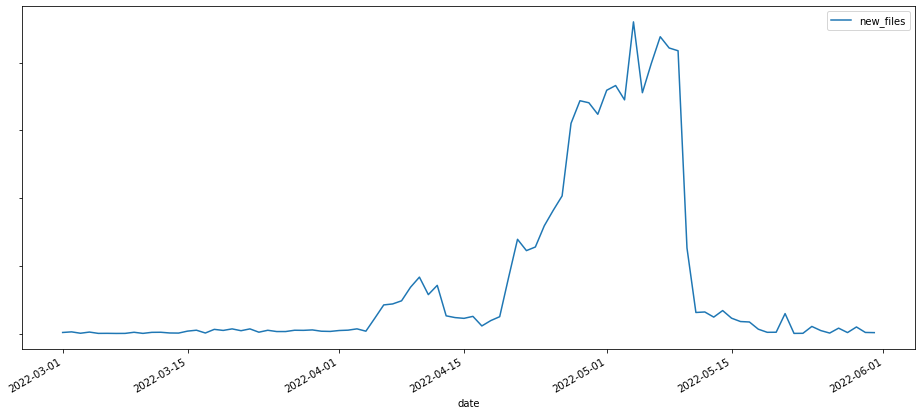
At the same time, the number of emails attaching malware files increased, mostly due to spam campaigns distributing common malware (like lovgate and noon). We observed a high peak of formbook and AgentTesla samples in January 2022:
Additionally, the adoption of exploits keeps its growing trend for the last five years, however at a lower rate than it did in 2021. Indeed, in 2021 we observed a peak in the number of different CVEs exploited by new malware samples.

Total of CVEs exploited by new samples per year
Overall, the count of new malware samples exploiting CVEs hasn't changed much during the last three years. Only 5% of the CVEs tagged in 2022 were related to vulnerabilities published the same year, compared to a 7.8% in 2021. The following graph shows the 2022's top ten exploited CVEs by number of samples.
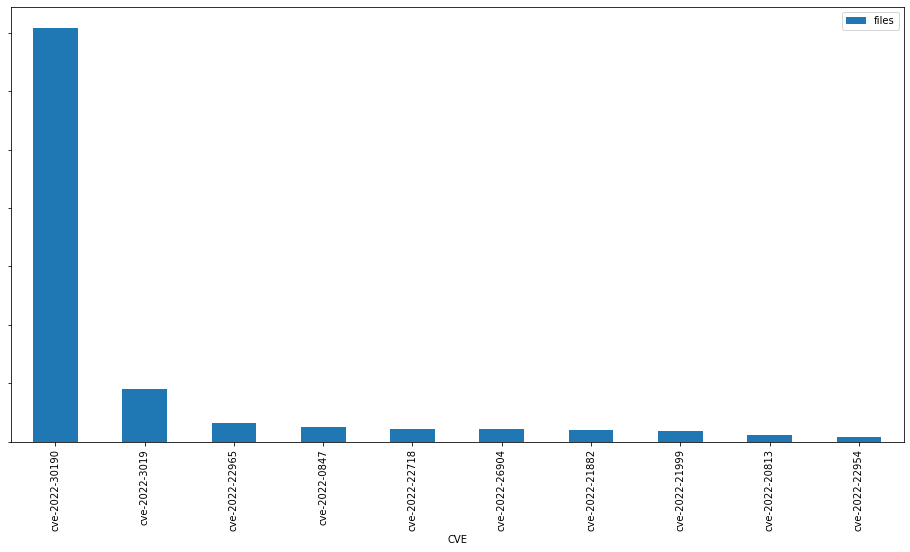
CVE-2022-30190 (aka Follina) was the most exploited new CVE in 2022. This vulnerability affects the Microsoft Windows Support Tool and allows attackers to remotely execute code in the compromised machine. We wrote about this vulnerability some months ago in our blog.
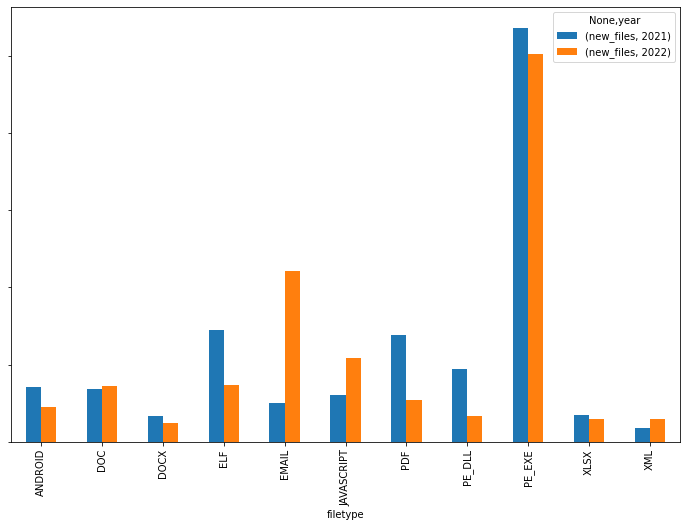
Additionally, we observed an increase in the number of email, android, javascript and xml file types exploiting vulnerabilities. Some of the most popular CVEs for these file types in 2022 were CVE-2017-11882 (20 year old MS Office vulnerability patched in 2017), CVE-2017-0199 (MS Office/WordPad RCE vulnerability) and the most recent CVE-2022-30190 (aka Follina). This might indicate the adoption of Follina into kits used to weaponize attachments that would still keep the old exploits.
The number of new PE, ELF, Android, PDF, XLSX and DOCX files exploiting vulnerabilities decreased in 2022 when compared to 2021. However, the number of DOC, Email (attachments), Javascript and Text files (scripts, such as powershell), increased:
Number of samples exploiting vulnerabilities by file type (2021 vs 2022)
As we discussed in our VirusTotal's 2021 Malware Trends report, we observed a shift from Microsoft Word to Excel files as a way to carry malicious macros. The difference in the number of new files was significatively bigger during the first half of the year, probably due to Emotet heavily distributing excel files with malicious macros during this period.
Excel vs Word files exploiting vulnerabilities in 2022

First thing that caught our attention was the apparently vanishing of Dridex from the Top10 in 2022. On the other hand, Mirai is surprisingly active. We observed a high peak of Linux sample submissions around May 2022 corresponding to a Mirai burst. A peak in lookups for these samples during the same period confirms users’ interest. One of Mirai’s recent attacks was a DDoS attack against Minecraft Wynncraft.
For RATs and backdoors the landscape hasn't changed much since 2021. Padodor/Berbew is still at the top, together with Bladabindi, Gh0strat, FlyAgent, Zegost, DCRat and RemcosRAT as it can be seen in the following chart.
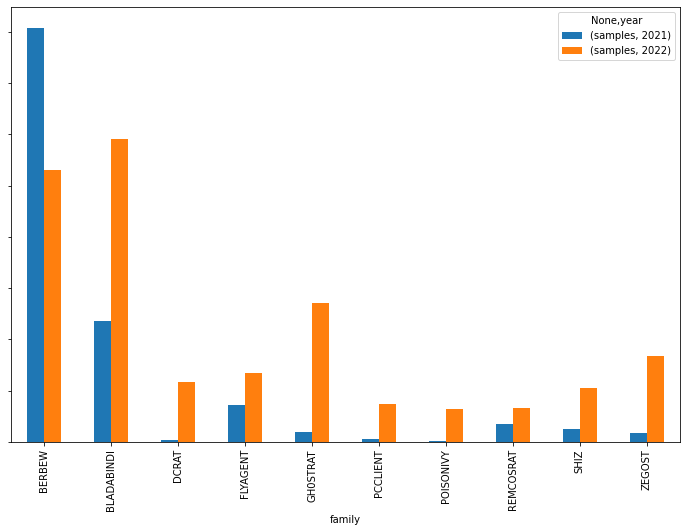
In 2022 we found old and new contenders. Bladabindi, Gh0stRat, FlyAgent, RemcosRAT and Shiz increased their presence in the top10, while others like AsyncRat, DarkComet, QuasarRAT or RBOT are out of the ranking, replaced by DCRAT, PCCLIENT, POISONIVY and Zegost
We also detected an increase in the number of malware samples using LOLBIN ("Living Off the Land BINary") legitimate operating system files to camouflage malicious activity or take advantage of already implemented functionality. The percentage of malware samples using lolbins shows a continuous increase.
We can find traces of these lolbins files in the VTI interface, under different sections in the behavior report: process created, command executions, modules loaded, registry keys set key/value, etc.
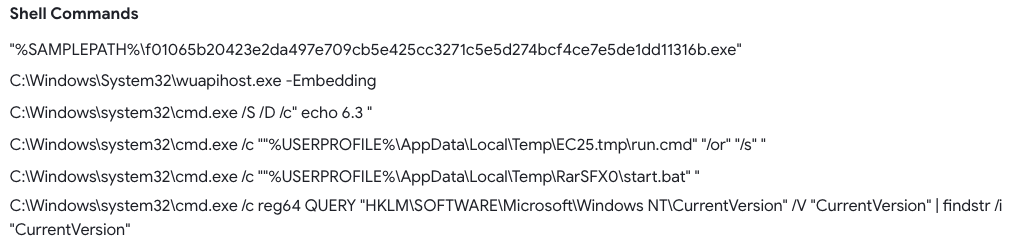
A list with the most common lolbin files used in malware samples in 2022 includes update.exe, cmd.exe, installutil.exe, sc.exe, at.exe, certutil.exe, msiexec.exe and msbuild.exe.
The first graph is based on the actor attribution we find in Collections. It shows the number of samples first seen in 2022 included in collections belonging to different threat actors. To minimize noise, we excluded samples belonging to common software toolkits used by threat actors in their operations (like CobaltStrike).
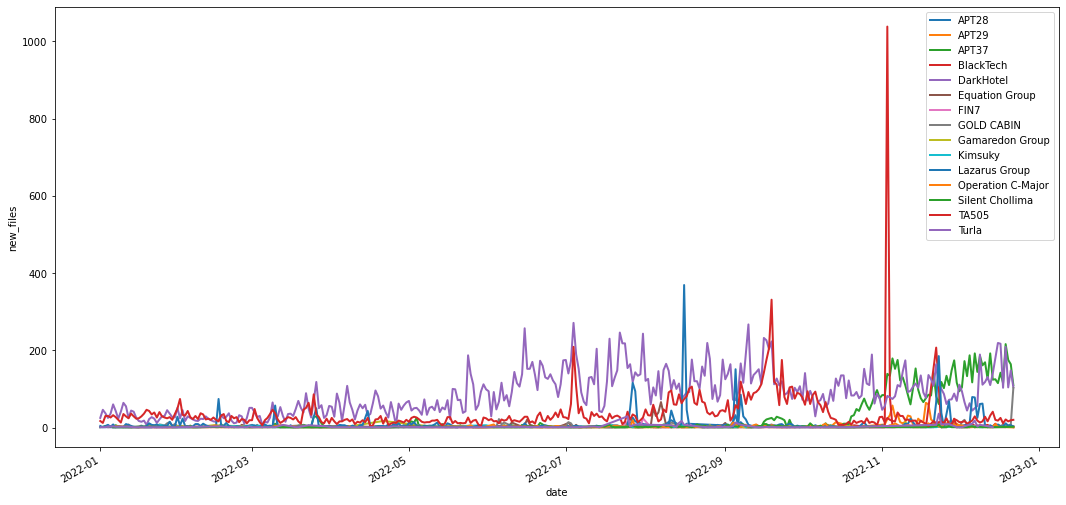
The graph shows a very active BlackTech from July to October and at the beginning of November, most samples related to the SpiderPig RAT collection. Other actors like DarkHotel had a continuous stream of submissions during the year, mainly through Jaku samples attributed to this actor by Malpedia. The Lazarus Group is the most prolific group in terms of the number of new collections attributed to them.
Now back to Cobalt Strike, this is one of the most used artifacts by different actors, including but not exclusive to APT32, APT41, FIN7 or APT29. June 2022 was the most active month of the year in terms of new files attributed to Cobalt Strike in VirusTotal.
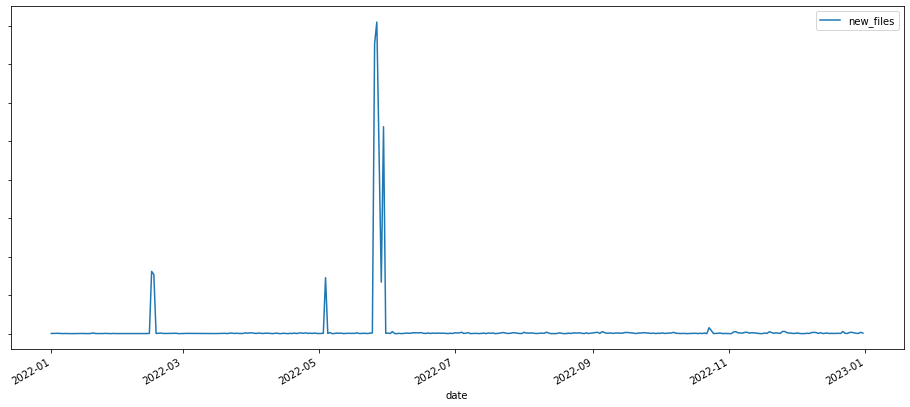
Last year we added 165 yara rules that helped to shape this collection. In fact, 99% of the files in this collection are detected by any of the Crowdsourced Cobalt Strike Yara rules available in VirusTotal. Last year we also saw the discovery of cracked Cobalt Strike versions in the wild that probably contributed to the proliferation of this artifact in malware campaigns.
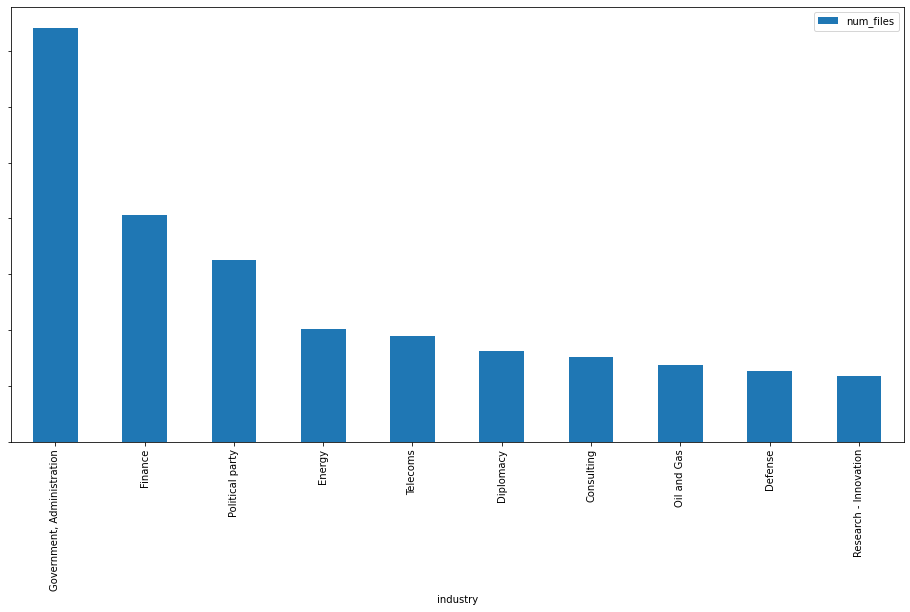
Finally, OSINT Collections victimology also shed some light on potential victimology. According to this data, the top10 rank of preferred targeted industries by attackers in 2022 is as follows:
According to the same source the following are the top five territories impacted by malicious activity: (1) Ukraine, (2) Russia, (3) United States, (4) South Korea and (5) Vietnam.
As a very brief summary, email as a distribution vector hosting suspicious PDFs in external hosting was an unexpected return to the past. The rotation in exploitation techniques seems to follow whatever works better for attackers given the quick adoption of any exploit, with some outliers such as Follina. It is also interesting comparing the scale of some threats that we sometimes tend to underestimate just because they became ubiquitous, with examples such as Mirai or Zloader. LOLBINs seem to keep growing in terms of internal monitoring to avoid lateral movement. Finally, Collections offer a OSINT-based high level overview of actors and victimology.
At VirusTotal, we will keep sharing both our visibility and best practices to protect against new attacks and to keep our world a little bit safer. As usual, we are happy to hear from you.
Happy hunting !
Distribution vector evolution
During 2022 we detected changes in the way malware is distributed. First, the number of URLs used in phishing attacks has doubled since 2021, and the number of emails distributing any kind of malware increased from 11.4% in 2021 to 26.5% in 2022, that is a 132% increase.This seems to correlate with the huge increase (almost doubled compared to 2021) of malicious PDF files hosted in phishing URLs. Probably this combination was one of the main distribution vectors of fraudulent content in 2022.
At the same time, the number of emails attaching malware files increased, mostly due to spam campaigns distributing common malware (like lovgate and noon). We observed a high peak of formbook and AgentTesla samples in January 2022:
Additionally, the adoption of exploits keeps its growing trend for the last five years, however at a lower rate than it did in 2021. Indeed, in 2021 we observed a peak in the number of different CVEs exploited by new malware samples.
CVE-2022-30190 (aka Follina) was the most exploited new CVE in 2022. This vulnerability affects the Microsoft Windows Support Tool and allows attackers to remotely execute code in the compromised machine. We wrote about this vulnerability some months ago in our blog.
Additionally, we observed an increase in the number of email, android, javascript and xml file types exploiting vulnerabilities. Some of the most popular CVEs for these file types in 2022 were CVE-2017-11882 (20 year old MS Office vulnerability patched in 2017), CVE-2017-0199 (MS Office/WordPad RCE vulnerability) and the most recent CVE-2022-30190 (aka Follina). This might indicate the adoption of Follina into kits used to weaponize attachments that would still keep the old exploits.
The number of new PE, ELF, Android, PDF, XLSX and DOCX files exploiting vulnerabilities decreased in 2022 when compared to 2021. However, the number of DOC, Email (attachments), Javascript and Text files (scripts, such as powershell), increased:
As we discussed in our VirusTotal's 2021 Malware Trends report, we observed a shift from Microsoft Word to Excel files as a way to carry malicious macros. The difference in the number of new files was significatively bigger during the first half of the year, probably due to Emotet heavily distributing excel files with malicious macros during this period.
Malware artifacts and toolsets
We explored how some common malware artifacts and tool sets evolved in 2022. This includes botnets, pentesting tools such as meterpreter, and common operating system tools like powershell or autoit used for lateral movement.First thing that caught our attention was the apparently vanishing of Dridex from the Top10 in 2022. On the other hand, Mirai is surprisingly active. We observed a high peak of Linux sample submissions around May 2022 corresponding to a Mirai burst. A peak in lookups for these samples during the same period confirms users’ interest. One of Mirai’s recent attacks was a DDoS attack against Minecraft Wynncraft.
For RATs and backdoors the landscape hasn't changed much since 2021. Padodor/Berbew is still at the top, together with Bladabindi, Gh0strat, FlyAgent, Zegost, DCRat and RemcosRAT as it can be seen in the following chart.
In 2022 we found old and new contenders. Bladabindi, Gh0stRat, FlyAgent, RemcosRAT and Shiz increased their presence in the top10, while others like AsyncRat, DarkComet, QuasarRAT or RBOT are out of the ranking, replaced by DCRAT, PCCLIENT, POISONIVY and Zegost
We also detected an increase in the number of malware samples using LOLBIN ("Living Off the Land BINary") legitimate operating system files to camouflage malicious activity or take advantage of already implemented functionality. The percentage of malware samples using lolbins shows a continuous increase.
We can find traces of these lolbins files in the VTI interface, under different sections in the behavior report: process created, command executions, modules loaded, registry keys set key/value, etc.
A list with the most common lolbin files used in malware samples in 2022 includes update.exe, cmd.exe, installutil.exe, sc.exe, at.exe, certutil.exe, msiexec.exe and msbuild.exe.
Threat Landscape
Last year we launched Collections as an actionable tool for strategic intelligence. You can learn more about them in our recent webinar. We analyzed this data to have a better understanding of the impact of malicious campaigns in 2022.The first graph is based on the actor attribution we find in Collections. It shows the number of samples first seen in 2022 included in collections belonging to different threat actors. To minimize noise, we excluded samples belonging to common software toolkits used by threat actors in their operations (like CobaltStrike).
The graph shows a very active BlackTech from July to October and at the beginning of November, most samples related to the SpiderPig RAT collection. Other actors like DarkHotel had a continuous stream of submissions during the year, mainly through Jaku samples attributed to this actor by Malpedia. The Lazarus Group is the most prolific group in terms of the number of new collections attributed to them.
Now back to Cobalt Strike, this is one of the most used artifacts by different actors, including but not exclusive to APT32, APT41, FIN7 or APT29. June 2022 was the most active month of the year in terms of new files attributed to Cobalt Strike in VirusTotal.
Last year we added 165 yara rules that helped to shape this collection. In fact, 99% of the files in this collection are detected by any of the Crowdsourced Cobalt Strike Yara rules available in VirusTotal. Last year we also saw the discovery of cracked Cobalt Strike versions in the wild that probably contributed to the proliferation of this artifact in malware campaigns.
Finally, OSINT Collections victimology also shed some light on potential victimology. According to this data, the top10 rank of preferred targeted industries by attackers in 2022 is as follows:
According to the same source the following are the top five territories impacted by malicious activity: (1) Ukraine, (2) Russia, (3) United States, (4) South Korea and (5) Vietnam.
Conclusions
A high-level vision of the malware ecosystem serves different purposes, including understanding how to prioritize monitoring and prevention, optimize security stack, resource allocation, brief CTI and IR teams, and polish the security strategy.As a very brief summary, email as a distribution vector hosting suspicious PDFs in external hosting was an unexpected return to the past. The rotation in exploitation techniques seems to follow whatever works better for attackers given the quick adoption of any exploit, with some outliers such as Follina. It is also interesting comparing the scale of some threats that we sometimes tend to underestimate just because they became ubiquitous, with examples such as Mirai or Zloader. LOLBINs seem to keep growing in terms of internal monitoring to avoid lateral movement. Finally, Collections offer a OSINT-based high level overview of actors and victimology.
At VirusTotal, we will keep sharing both our visibility and best practices to protect against new attacks and to keep our world a little bit safer. As usual, we are happy to hear from you.
Happy hunting !
