Ryuk is one of the most dangerous Ransomware families. It is (allegedly) run by a specialized cybercrime actor that during the last 2 years mainly focused on targeting enterprise environments. The amount of bitcoins demanded in their ransom attacks varies depending on the target. Some of the wallets used by the group to collect the ransom payments reached millions of dollars in a few weeks.
Protecting against such attacks is one of the main priorities for any CISO or security team. This is a problem that should be approached from different perspectives, being prevention (likely) the most relevant one.
Now, what can be done in terms of prevention? Information is power, the first thing we need is understanding how the new campaigns are operating. Is this distributed through phishing or exploiting any vulnerabilities? Do they use brute force attacks? Maybe all together?
In addition to the TTPs described above, we want as many technical details as possible. This will result in very valuable Indicators of Compromise we can use for protecting our infrastructure: deploying networking indicators to disrupt malware communication, making sure our Yara rules will detect all the components of the attack, launching regular scans in our infrastructure to detect any artefact used in the campaign.
We need to quickly deploy our fishing nets to catch everything related to fresh new campaigns! And then to keep monitoring for a while to make sure we keep our systems updated as attackers evolve.
In this blogpost we will describe how we used VirusTotal to detect and monitor new Ryuk activity. However this is a very specific case where we want to show how our IDA plugin can save us a lot of time when dealing with certain samples.
If you want to learn more about how you can keep your organization safe from ransomware and how to easily leverage VirusTotal to monitor ransomware activity, please join us for our next Anti-ransomware workshop -
English (Live November 4th, 1pm ET) and
Spanish (Live October 28th, 17:00 CEST) versions available.
Starting the investigation
Two weeks ago new files were uploaded to VirusTotal (
1,
2). According to the
crowdsourced YARA rule that identified them, these files looked like Ryuk malware.
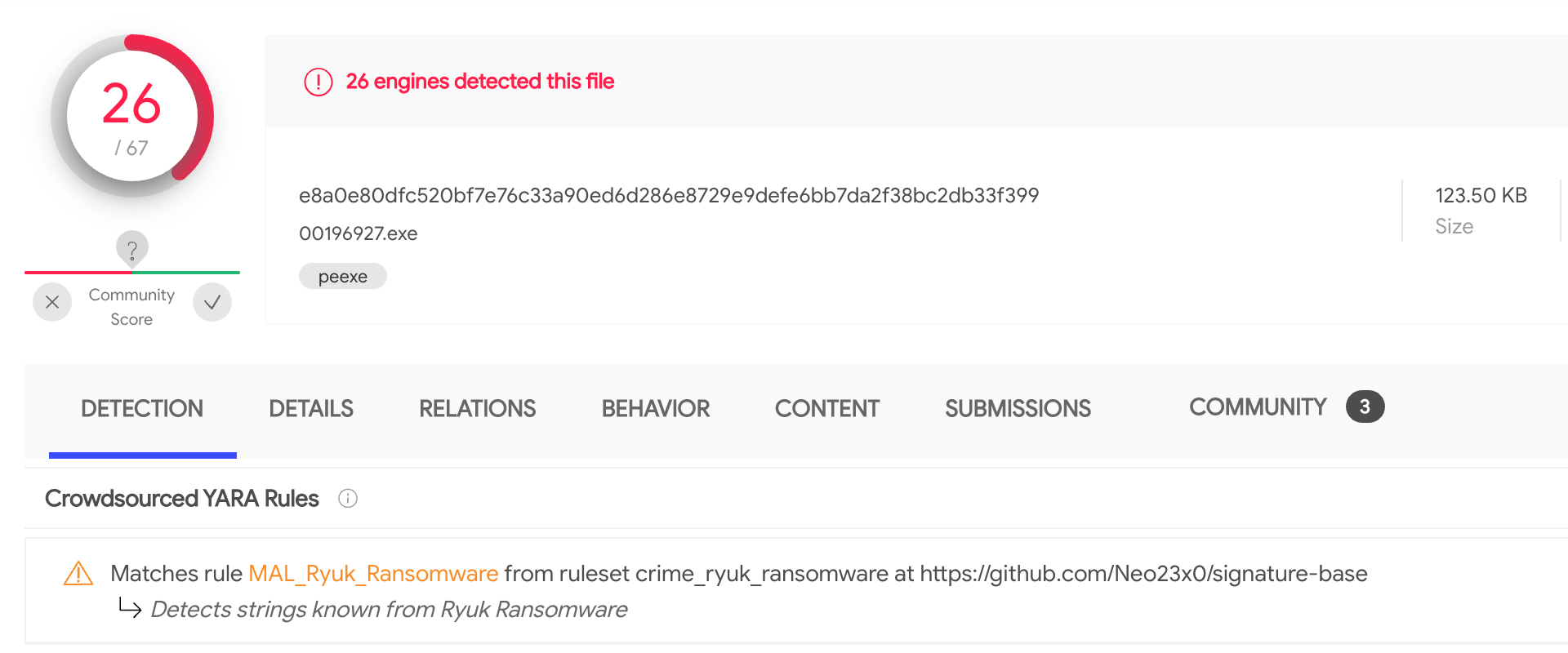
A closer look revealed that these samples have been probably dumped from memory: the disassembled code showed plenty of memory mapped addresses, the import table was missing and the samples crashed when executed - they were definitively corrupted PE files.
Given these were fresh samples, we certainly wanted to know more about them, especially if they were part of a bigger campaign. In such cases, one of our best allies is looking for similar samples that could also be part of the attack. However, when working with memory dumps we need to be careful, given that probably some segments and memory mapped addresses will be execution specific. If we include any of such specifics in our search, we won't be able to find other samples.
IDA plugin to the rescue
One of the options would be to rebuild the samples we found, which is an extremely time consuming process. Instead, we can use the
VirusTotal IDA plugin (
see original blog post announcement) to help us search for the original sample. Using the "search for similar code" functionality we can create a query that will ignore all the memory mapped addresses, being a perfect choice for our problem.
Taking a look at the samples with IDA, we can see there are many functions that aren't properly identified by the disassembler engine given the use of anti-disassembly techniques. Precisely for this reason, they are good choices for searching for code similarity.

We just need to select the code, right-button, and search for similar code. The resulting query will take care of ignoring all the memory mapped addresses we wanted to get rid of.
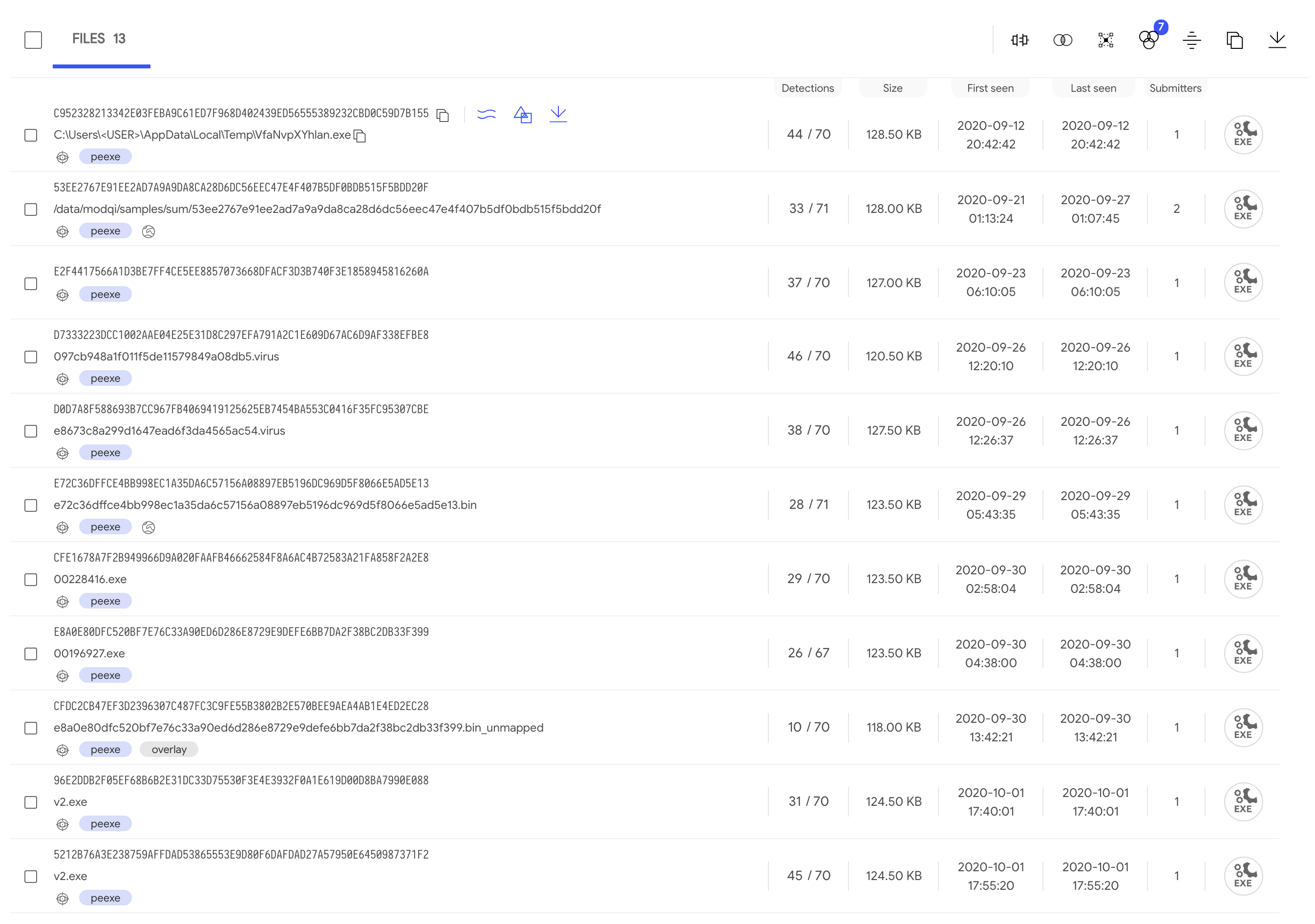
The resulting listing with all the
files found shows very close first submission time. Also, some of them report behaviour activity, meaning they executed in the sandboxes without crashing: maybe one of them could be our original sample.
Picking
one of our initial samples and
another one with behavioural information, we can see that:
- They don't show up as similar when doing a similarity search (as expected).
- They have some long sequences of bytes in common.
Is this our sample?
At this point we feel confident that the new sample found is the one we were looking for. Indeed, starting from this sample and taking a look at the (undetected) function located at
0x35008A60, we select a large sequence of instructions with the IDA plugin (as we did before) for a new search. This results in only 4 files that match the
query generated: our two initial samples, another file that's also corrupted, and the previously chosen sample that detonated in our sandboxes. Therefore, this is the second time that we get this file when looking for similar code.
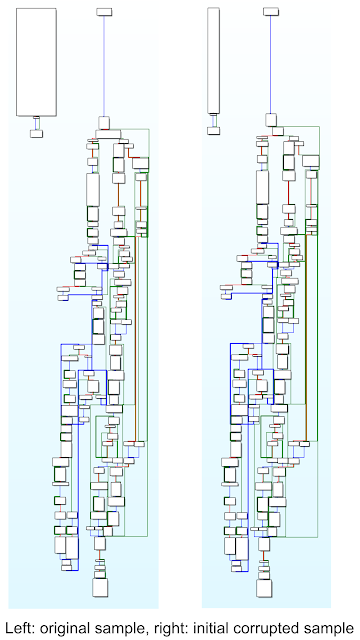
Going deeper, we'll see that it shares the same PE entry point that our two initial corrupted files. Furthermore, their WinMain functions are the same. Initially it looks like a quite simple function, composed of only three blocks of code. But, after overcoming the anti-disassembly trick implemented to confuse IDA, we can compare both function graphs to see the similarity. We conclude that we found the original sample.
What now?
At the time of this research there isn't any Yara rule detecting the original sample and it has 28/71 positives. Inside this file we can find encrypted strings that are extremely useful for pivoting to find additional samples. These strings are included in the corrupted files as well, stored in the ".gfids" segment at the end of the file. In other words, they aren't located in the ".data" segment as seen in the original sample. This new location reveals that probably these strings were initially encrypted and became decrypted after execution, thus they can be seen as footprints of the original sample.

Using the VT-IDA plugin we can search for
other files that contain these encrypted strings. As expected, the four files found before are listed now, but there are two other samples that were submitted three days prior to our original sample and can also be investigated.
Moreover, all these new strings can be used to improve the original Yara rule that brought us here, or to create a new one! Remember to keep it running as a LiveHunt to make sure you keep track of any new Indicators of Compromise and to detect anything new attackers use in their campaigns. You can find all the details about the campaign described in this blogpost in the
following VT-Graph.
This post was co-authored by Vicente Diaz.
