In their own words:
NSFOCUS POMA, as an integral part of the NSFOCUS Threat Intelligence (NTI) system, is a cloud‐based malware analysis engine built by the NSFOCUS Security Lab. It can take various types of files and perform both static and dynamic analysis on them to detect potentially malicious behavior, and produce analytic reports in many formats (including STIX). This service can help a user to protect his environment from various threats, such as 0‐day attacks, advanced persistent threats (APTs), ransomware, botnets, cryptocurrency mining and other malware.
We are very honored and proud to bring such values to the VirusTotal users and community.
Here are a few examples:
https://www.virustotal.com/gui/file/a01b10ae6e81c4efc7c4a7b0a6c893907e4a6044b87ed72be7e5800ae104c8c8/behavior/NSFOCUS%20POMA
https://www.virustotal.com/gui/file/d7dd7c2482b3d38cd7fae5860eaa912f019a31fb4988f8320a105c9c4ca5ebbd/behavior/NSFOCUS%20POMA
https://www.virustotal.com/gui/file/430aa2f84cc7934cabdb644eccbdb9d8355899ed9665570bc80b58fd4c010150/behavior/NSFOCUS%20POMA
You can find the sandbox behaviour reports on the behavior tab.
Threat Summary
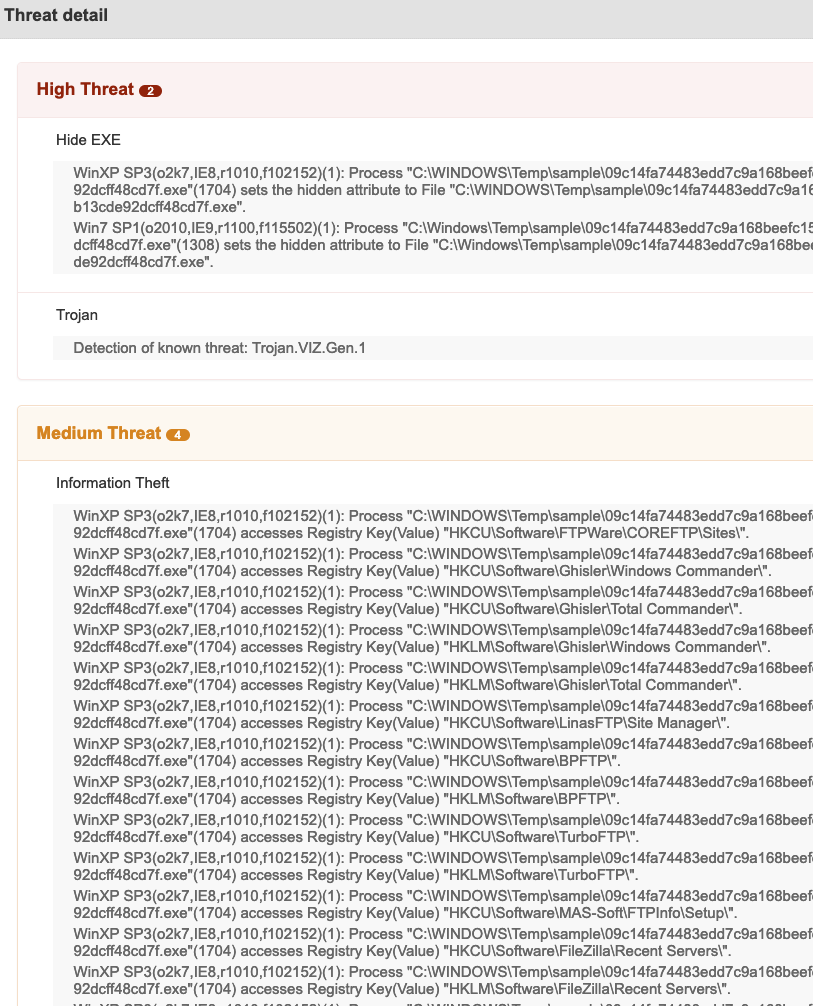
At the top of the detailed report, right away we can see a summary of the detection.Threat Detail
Within the threat detail section we can see the behavior in both Windows XP SP3 and Windows 7 SP1 ordered by risk, most important at the top.
Registry actions:
Registry actions:
Within the behaviour report we can see an interesting UUID
Connecting the dots
Within VTGraph we can visually see the relationships between this sample, the IP address, domains and URLS that we know about

0 comments:
Post a Comment