In their own words:
DOCGuard is a malware analysis service, whose main use case is to integrate with SEGs (Secure Email Gateways) and SOAR solutions.
The service performs a new kind of static analysis called structural analysis. The structural analysis dissembles the malwares and passes it to the core engines with respect to file structure components. By the aid of this approach, DOCGuard can precisely detect the malwares and extract the F/P free IOCs and may also identify obfuscation and encryption in the form of string encoding and document encryption.
The currently supported file types are Microsoft Office Files, PDFs, HTMLs, HTMs, LNKs, JScripts, ISOs, IMGs, VHDs, VCFs, and archives(.zip, .rar, .7z etc.). The detailed findings of the structural analysis are presented in an aggregated view in the GUI and can be downloaded as a JSON report and can also be gathered over API.
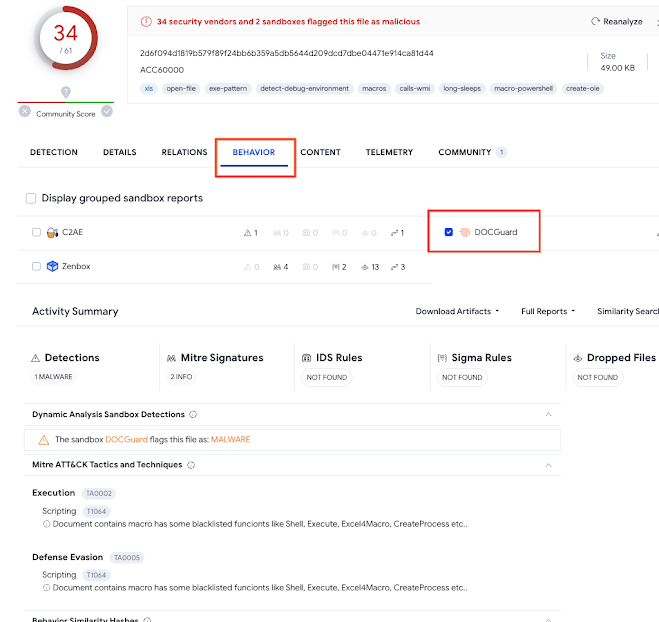
Going further, users can explore the behavior tab of the file scanned for more details. In the example below, we see a detected macro of a malicious Excel XLS file
In a malicious document, we can see memory pattern urls.
9cd785dbcceced90590f87734b8a3dbc066a26bd90d4e4db9a480889731b6d29
Additional examples:
- XLSX Spreadhseet with embedded domain 8ab6573a88155364fee4d6631781c0390c094c3cc99cb8b1f78c98f6c2aaf4b6
- XLS Spreadsheet d9ffac92ef7bf74d4982b1d82c591fc20e417194ea4813cd9f50ea5b442cb2de
- DOCX 754368ba0516ab324e2cffbad47937a086a4d50dd8ea4626761dd2583b23e580
- PDF 9d0d895f43c0967b15f610cec45dccb68d27de9eb538cca171648886e1307815
We believe that our integration with DOCGuard is a valuable addition to our platform and we are excited to offer this new service to our community. If you have any questions, please do not hesitate to contact us.